Services

The specifications of security management, policies, operations, and processes, as well as network configurations and software architecture to safeguard other cardholder data
read more

ISO 27001 Certification provides a management for implementing an information security management system to ensure the integrity, confidentiality and availability
read more

IT service management called ISO 20000-1 describes the criteria for creating, implementing, maintaining, and improving an IT service management system
read more

Fast-track incident response with an interactive view of your threat landscape
read more

Discover Your Assets with the Hacker Mindset You do not want your security measures to be insufficient when things change in the dynamic infrastructure of your organization. Track your digital assets in real-time and know your attack surface and protect it from attackers. Gain visibility into your ever-growing attack surface See Your Attack Surface Through […]
read more

Minimize Risk of Misconfigured Buckets IT resources, and apps- are now stored in the cloud. Of course, this migration had an inevitable result, such as widening the attack surface. Added to this was that organizations did not meet all the requirements in the process of moving to the cloud, and the misconfigured buckets issue became a significant threat. Types […]
read more

SOC Platform enables end-to-end visibility from edge to cloud Consolidate TIP and SOAR, collaborate seamlessly, and prevent attacks with intelligent, orchestrated response. Access your data, no matter where you are Leverage the Platform Integration Leverage the platform from anywhere, whether you’re on-premises, at home, in your data center or a combination of them all with […]
read more

Cyber Threat Intelligence Cyber threat intelligence refers to a dynamic, adaptive technology that leverages large-scale threat history data to proactively block and remediate future malicious attacks on a network Importance of Cyber Threat Intelligence Cyber threat intelligence itself is not a solution !! Cyber threat intelligence itself is not a solution, but it is a […]
read more
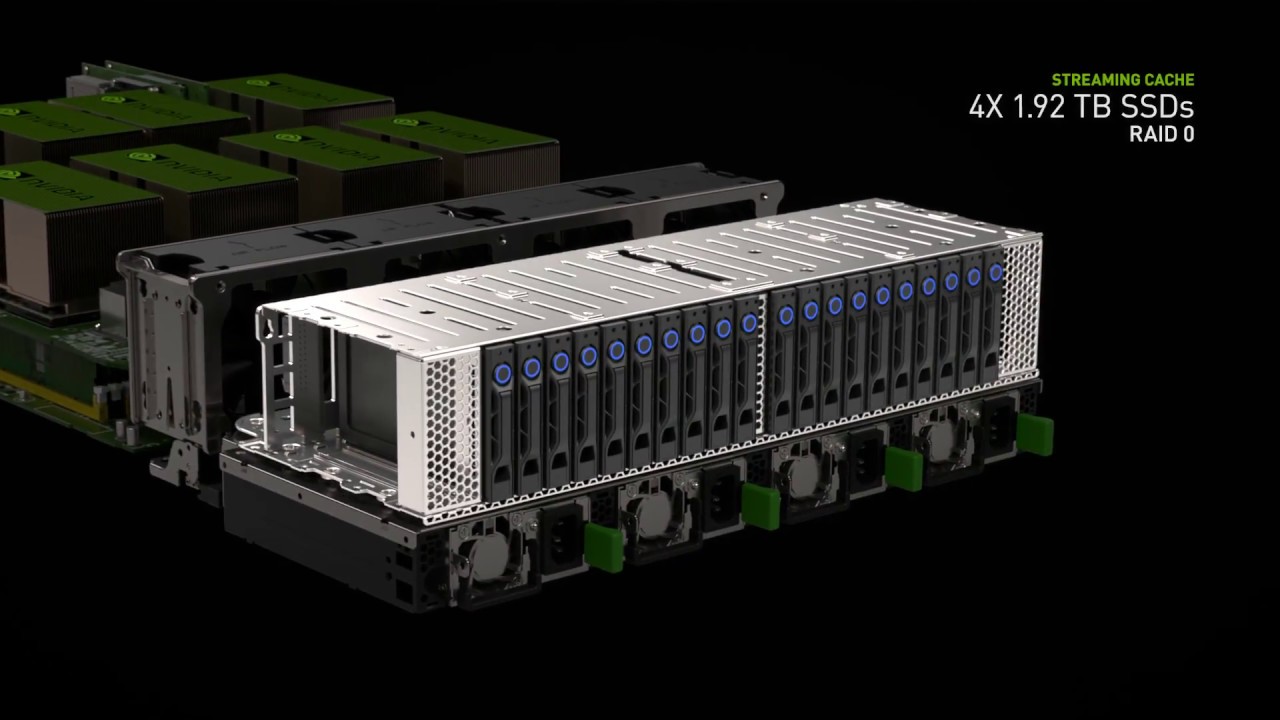
The Proven Standard for Enterprise AI Built from the ground up for enterprise AI, Our solutions platform combines the best of software, infrastructure, and expertise in a modern, unified AI development solution that spans from the cloud to on-premises data centers. Experience the Benefits of the Platform The Fastest Path to AI systems and the Cloud […]
read more

Fraud protection techniques have advanced rapidly over the past decade to keep pace with fraudsters preying on emerging weak points. Bad actors have taken full advantage of the online world’s increasing fragmentation as consumers and businesses alike interact across dozens of channels. Banks, businesses and others still have numerous fraud problems to address, from text-based […]
read more

What is VAPT? Vulnerability Assessment and Penetration Testing (VAPT) is a term used to describe security testing that is designed to identify and help address cyber security vulnerabilities. The meaning of VAPT can vary from one geographical region to another, either as a bracket for multiple distinct services, or a single, combined offering. VAPT as […]
read more

Transform into an AI enterprise with essential infrastructure. AI is powering mission-critical use cases in every industry—from healthcare to manufacturing to financial services. The Archeturure of POD™ reference architecture provides the critical foundation on which business transformation is realized and AI applications are born
read more

AI for Intelligent Automation and Acceleration leverages our award-winning AI technology for intelligent automation and acceleration of laborious tasks and processes, saving as much as 90% of human time compared to traditional MSSPs. Best quality and best price of service AI Platform Use Cases Risk-Based and Threat-Aware Application Security Testing (AST) Read More Advanced AST Web, Mobile, […]
read more

IT audit information technology audit An IT audit is the examination and evaluation of an organization’s information technology infrastructure, policies and operations. Information technology audits determine whether IT controls protect corporate assets, ensure data integrity and are aligned with the business’s overall goals. IT auditors examine not only physical security controls, but also overall business and financial controls that involve information […]
read more

Business continuity is an organization’s ability to maintain essential functions during and after a disaster has occurred. Business continuity planning establishes risk management processes and procedures that aim to prevent interruptions to mission-critical services, and reestablish full function to the organization as quickly and smoothly as possible. What is business continuity and why is it important? The most […]
read more

A policy defines a guide of action to achieve an organization’s goals and objectives. A good policy explains rules, the importance of rules, who the rules cover, how the rules are enforced, and describes consequences of abandoning rules in a clear and easily understood manner. An IT policy defines how an organization develops, implements, and […]
read more

Log analysis is the process of reviewing, interpreting and understanding computer-generated records called logs. Key takeaways Log analysis functions manipulate data to help users organize and extract information from the logs. Organizations that effectively monitor their cyber security with log analysis can make their network assets more difficult to attack. Log analysis is a crucial […]
read more
Nothing Found!
Can't Find What You Are Looking For?
Tell us what you're looking for and we'll make it for you . Contact us!
